Company Blog
Very Sneaky Seasonal Virus Emails
Posted by admin in Threat Warning on December 5, 2013 with No Comments
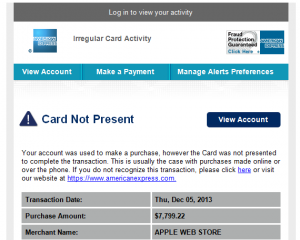
I just received several VERY SNEAKY season-related emails that have links to viruses in them. Beware of emails from credit card companies (Amex in this case) that claim fraudulent charges or compromised account data. The one listed here indicates that a “cardless transaction” to the online Apple Store was processed. The key to avoiding this virus is noticing that the links in the email DO NOT point to the American Express website. DO NOT click these links or open files they download to your computer. If you’ve already done so, contact a computer professional immediately before more damage is done.
Most phishing schemes and virus emails come from known, but unexpected companies (FedEx, UPS, PayPal, etc.). If you didn’t purchase anything recently, it might raise enough suspicion for you to double-check the email before clicking any links. This time of year, people are ordering more online, and even expect to be notified of potential fraud. This creates a ‘perfect storm’ for even savvy users to fail.
We suggest that you hover your mouse over the links in the email to see where they point BEFORE opening them. Hovering over (not clicking) links in an email or website will typically display a small window with the destination address. Even if an email looks legitimate, we still recommend manually typing in the company’s website in your web browser instead of clicking links in emails. (i.e., open your web browser and type www.americanexpress.com)
Feel free to submit any questions or concerns you have via our Contact Form.
4 Elements of an Effective Backup
Posted by Carmine Inserra in Disaster Recovery on October 6, 2013 with No Comments
Disaster Recovery can refer to many different aspects of a business’s ability to function when they face an unexpected event. There are many types of events that can (and will) affect your ability to use or access your data. Here are a few situations you need to consider and prepare for:
• Deleted Data (Accidental or Malicious)
• Data or Software Corruption
• Hard Drive Failure
• Theft or Vandalism
• Fire or Water Damage
• Data Inaccessibility
Here are 4 things to consider when implementing or reviewing your Disaster Recovery Plan:
-
Recoverable Copies – You need to make sure to backup ALL of your critical data. Just because you click the checkbox next to the C: drive, doesn’t mean everything is getting backed up. Make a list of your critical software and ask your software vendor representative how they recommend backing up their data. For example: QuickBooks typically places their data in the Public user folder. Programs like TimeMatters use an SQL database that can’t be backed up without a special add-on for your backup. Email programs like Outlook typically store their data in hidden folders under your user profile. Also don’t assume your payroll company is backing up the data on your processing computer. ProSysCon technicians have experience backing up and recovering data for many different types of software.
-
Offsite Copy – Verify you have at least one copy of your data at a different geographical location. Most of our clients have considered a fire or flood, but what if you experience a close lightning strike causing a significant surge? Are you prepared if the business in the next suite sets off the sprinkler system, or if you have to immediately evacuate your premises for days or weeks? There are many simple and cost-effective ways to accomplish this.
-
Backup Revisions – Verify that you have multiple copies of your data that span a period of time. Multiple copies will protect you against deleting or changing a file that you might not realize for several backup periods. For example, you delete a file on Monday but don’t realize it until Thursday. If you ran 3 backups since the file was last changed, you need to make sure your backup system has enough space and retention to not have already overwritten it.
-
Test Your Backup – There’s no way to know your backup works if you don’t test it periodically. Checking backup logs on a regular basis is a good idea, but isn’t the same as actually restoring a file. If you aren’t familiar with how to test your backup, ask your IT professional to restore a specific file to demonstrate that it works.
ProSysCon gladly offers a complimentary cursory Tech Audit for potential clients. We find backup configuration issues in 80% of our Tech Audits, so if you’re not 100% sure your backup is configured correctly, let us check it to be sure. Contact Us today to schedule your complimentary Tech Audit!
ProSysCon Celebrates 10 Years!
Posted by Carmine Inserra in What's New on June 3, 2013 with No Comments
ProSysCon is proud to announce that this June marks our 10th anniversary in business! You may have noticed we have a new logo and business cards as well. In addition to these visible changes we’ve increased the power of our hosting platforms, updated our internal servers, and added a wide array of cloud-based solutions. It’s been an honor to serve you for the past decade, and we look forward to the next 10 years!

Recent Comments